Warning! The information and
tools listed on this site are for educational purposes only.
You should not use this information to harass people, or
for unethical reasons.
Intelligence Gathering & Security
This site aims to make you an online superhero. It will teach you
how to get the IP address from email headers, search images on the
web, trace IP address, and much more. After exploring ways to gather
intelligence on a target, we'll explore security fundamentals.
Note: This site is still young. Please come back soon for more content! Join our mailing list.
Learn how to use Google to it's full potential with these quick
tips.
Search Operators:
Search operators allow you to specify certain things when looking
something up, and have the syntax: operator:term,
where operator is the specific operator(more down below), and
term specifies what you're looking for.
site:[url] Search using only one url.
filetype:[pdf] Find file types that end with .pdf.
phonebook:[name] Find phonebook listings of [name].
allintitle:[term] Searches webpages with a specific
title.
allinurl:[term] Searches URLs for [term].
Equipped with a few simple operators, you can learn more down below.
Google Advanced Search
Moz.com Google Search Operators
"An Internet Protocol address (IP address) is a numerical label
assigned to each device connected to a computer network that uses
the Internet Protocol for communication. An IP address serves two
principal functions: host or network interface identification and
location addressing." -Wikipedia
Obtaining a person's IP adress is as simple as creating a website
for people to visit, or by using an online service, to name a few.
When someone connects, you'll be able to see an HTTP
GET
request from the IP address.
WHOIS Lookup
With a WHOIS lookup, you're able to see various things related to an
IP address, such as who it is registered to, the location, etc.
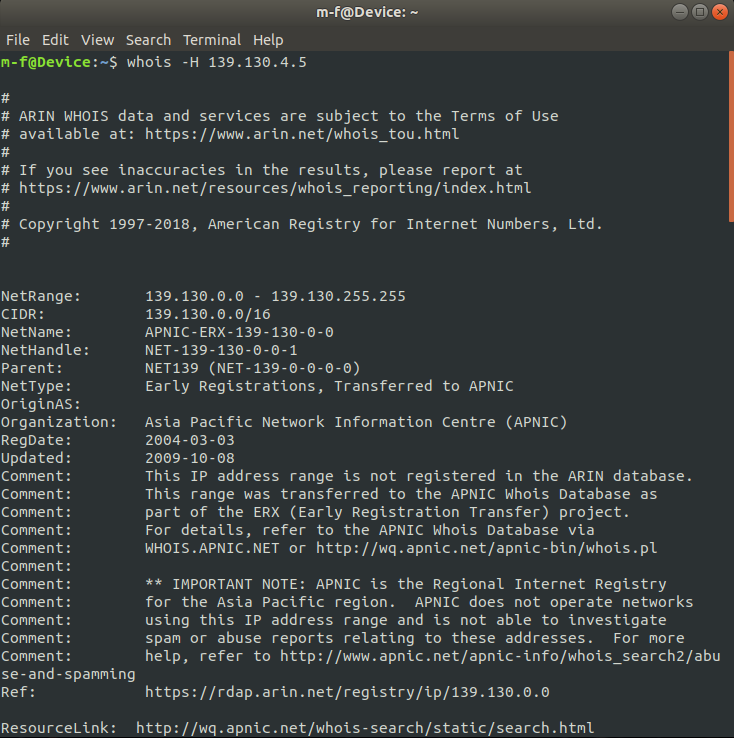
Example of a WHOIS lookup using the terminal.
Visit the
ICANN WHOIS Lookup Website.
Additional IP Address Tracking Tools
IPverse
IP2Location
IPfingerPrints
Public records include things such as: ownership of properties,
birth records, death records, criminal records, and much more. Below
are some useful links to aide you in your intelligence gathering.
General Information
-
Whitepages
- Find people, contact info, & background checks.
- Lullar
- People search by email or name.
-
Family Tree Now
- Research and build a family tree for free.
-
Radaris
-
Learn about people - background check, phone, address, email,
reverse phone, etc.
- Webmii
- Another people search engine.
-
Linkedin
-
Get people's work history, current job, education, location,
etc.
Social Security Numbers
Usernames
Email Investigation
Phone Numbers
Social media accounts are treasure chests for the intelligence seeker.
Locations, favorite bars, movies, books, pet names, family, you name
it, and you'll probably find it within a social media account. If
you're reading this, it'd probably be a good idea to run these tests
on your own accounts, and remove any revealing information, such as
pet's names, which are usually used as "security questions". If your
Mom is on your friends list, and she includes her maiden name, like so
many do, well, that's 2/2 questions into your account!
It is usually recommended to set up fake accounts for each of these
services. Keep in mind that this may violate the
terms of service on such platforms.
Facebook
Specifying information with the URL:
Places Visited:
facebook.com/search/[user_id]/places-visited
Places Checked-in:
facebook.com/search/[user_id]/places-checked-in
See posts from a specific location. Search: Posts
written in Orlando, FL
Search for a person within a location. Search:
[person] in Orlando, FL
Twitter
Instagram
Section coming soon...
Psychological Analysis
Get a glimpse into the common emotions expressed by a target.
"Computer security, cybersecurity or information technology
security (IT security) is the protection of computer systems from
theft or damage to their hardware, software or electronic data, as
well as from disruption or misdirection of the services they
provide." - Wikipedia
As you can see from the different sections below, security is a
large field. Below I've equipped you with enough information to
acquire a decent understanding. We'll start with the bare minimum,
and arguably one of the most important: physical security.
Do you leave your passwords and emails in a tablet next to your
computer? Is your computer easily accessible(e.g. can anyone start
it up, and view your file system)? You might want to consider your
physical security if you answered "yes" to these questions.
Big companies are notably weary of physical security. Shredding
passwords, and other documents, before being thrown in a dumpster
outside of their facility(See:
dumpster-diving). Server rooms are locked with the newest technology, such as hand
scanners, and anyone without a security badge will be unable to
access them. Even getting into a building will be complicated, if
physical security is being considered, though people have been able
to get into buildings, and retrieve data, by
social engineering.
Thus is physical security: being mindful of your device(s) and data.
Don't throw your old hard-drive in the trash, and surely don't sell
it, before properly wiping the data, or destroying it.
Further Reading:
Physical Security
Physical Security (Wikipedia)
Cross-Site Scripting (XSS)
Section coming soon...
The Recommended Reading below is anything to do with computers. From
programming, hacking, compilers, and beyond. Reading just one of the
books below will improve you.
Open Source Intelligence Methods and Tools: A Practical Guide to
Online Intelligence
-
This book partially inspired this website, I highly recommended
it.
The Web Application Hacker's Handbook: Finding and Exploiting
Security Flaws
-
Recommended by companies such as bugcrowd, this book is the holy
grail of web application security.
The Browser Hacker's Handbook
-
Masterfully explains the web browser, the most used software on
the planet. You will learn how the browser works, it's flaws,
etc.
Rtfm: Red Team Field Manual
-
Very useful. This little handbook equips you with quick
commands, from covering your tracks(clearing log files), to
basic commands in different operating systems, and much more.
The Tangled Web: A Guide to Securing Modern Web Applications
-
An entertaining, easy-to-read book on web application security.
You Don't Know JavaScript Series
-
Free to read online. Theoretical approach to learning
JavaScript. What is scope? Closure? The this keyword?
Find out in this series.
Eloquent JavaScript
-
Free to read online. Brilliant introduction to JavaScript.
C Programming Language, 2nd Edition
-
The C Programming Language is a computer programming book
written by Brian Kernighan and Dennis Ritchie, the latter of
whom originally designed and implemented the language, as well
as co-designed the Unix operating system with which development
of the language was closely intertwined.
Hacking Point of Sale: Payment Application Secrets, Threats, and
Solutions
-
Must-have guide for professionals responsible for securing
credit and debit card transactions. As recent breaches like
Target and Neiman Marcus show, payment card information is
involved in more security breaches than any other data type.

Social media accounts are treasure chests for the intelligence seeker. Locations, favorite bars, movies, books, pet names, family, you name it, and you'll probably find it within a social media account. If you're reading this, it'd probably be a good idea to run these tests on your own accounts, and remove any revealing information, such as pet's names, which are usually used as "security questions". If your Mom is on your friends list, and she includes her maiden name, like so many do, well, that's 2/2 questions into your account!
It is usually recommended to set up fake accounts for each of these services. Keep in mind that this may violate the terms of service on such platforms.
Facebook
Specifying information with the URL:
Twitter
Instagram
Section coming soon...
Psychological Analysis
Get a glimpse into the common emotions expressed by a target.